The May 2017 FBI report from the Internet Crime Compliant Center shows another increase of 8,260 victims of business email compromise. It is just a matter of time until you or one of your employees receive an email meant to trick them into sending your money to someone that does not deserve it.
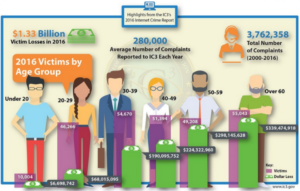
The FBI estimates the average loss of CEO fraud attacks at $25,000 to $75,000 per event. The report included this infographic to show losses by age groups.
Here is an example from one of my clients. 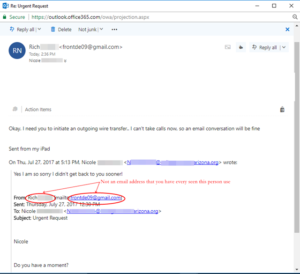 The person that received the message determined the message was a scam. That is great for her company. Are all of your employees educated on what to look for in email scams? Did you know that you can get free training videos from phishme. The typical video last just 5 minutes. It gives effective training that can make everyone aware of deceptive email messages.
The person that received the message determined the message was a scam. That is great for her company. Are all of your employees educated on what to look for in email scams? Did you know that you can get free training videos from phishme. The typical video last just 5 minutes. It gives effective training that can make everyone aware of deceptive email messages.
The IC3 report listed 12,000 reported incidents of the CEO fraud scheme in 2016. This scheme includes an email from the company CEO or CFO that requests a money transfer that needs to be done today. The email never comes from a business executive is uses the name or email address of a business executive. The CEO or CFO does not know about the message. It is easy to just call until you contact the person to verify the transaction.
The US Department of Justice suggests these action before you have a computer breach:
- determine which of you data, assets, and services warrants the most protection
- have a plan in place for computer intrusions
- have technology and services available for a cyber security incident
- have a company policy that allows network monitoring
- ensure your legal counsel is familiar with technology and cyber incident management
- adopt human resource policies that reduce the risk of cyber incidents
- establish a relationship with your local federal law enforcement offices before you suffer a cyber incident
- Establish Relationships with Cyber Information Sharing Organizations
The complete document is available at Cybercrime Unit.