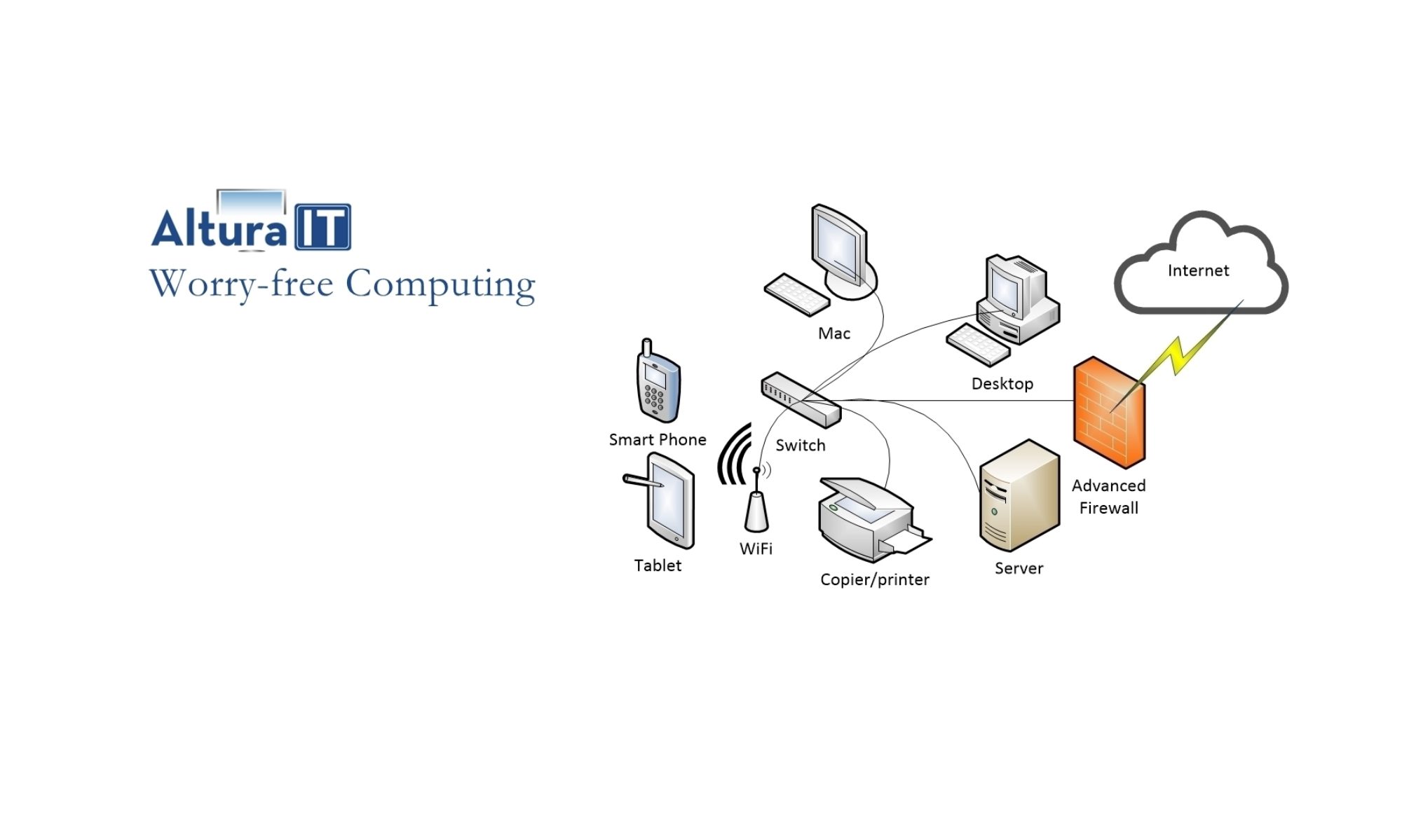
What does this mean?
The graphic above is created by Kaspersky, a global security company with a total market share of 8.14% in 2018. Lines on the globe show malware and system attacks detected by Kaspersky software products. You are seeing less than 10% of the activity world wide.
What the image shows
- The green OAS, On Access Scan, lines shows malware detected by Kaspersky software while files are opened, run, copied or saved on a computer or to a web file service.
- The red ODS, On Demand Scan, lines shows malware or viruses detected by a scheduled Kapersky scan.
- The orange MAV, Mail Anti-Virus scan, lines shows malware or virus detection from email messages that are detected as harmful.
- The blue WAV, Web Anti-Virus Scan, lines show any malware or viruses detected browsing web sites by a user protected by Kapersky.
- The pink IDS, Intrusion Detection System Scan, lines shows network attacks from a firewall on a computer.
- The yellow VUL, Vulerablity Scan, lines detect weak security settings or configurations on the current machine. An example would be to have any program on a flash drive run automatically when the drive is inserted.
- The purple KAS, Anti-Spam, lines detect suspected spam traffic sent to or from your computer.
- The teal BAD, Botnet Activity Detection, lines show a connection to a know command and control server used by cyber criminals.
How does this affect me?
Ransomware attacks occur every 14 seconds – Cybercrime Magazine. There are 32.5 million businesses in the US. That means every month your business could be attacked by some ransomware product. ( In 644 hours an attack every 14 seconds could reach every business in the US. There are 730 hours in one month)
Are you prepared?
- Do you have know good and tested backups of your data?
- Are your files automatically synced to your online backup?
- Does your online backup site have file versioning to keep multiple copies of the same file?
- Are all of the available software patches installed in all of the programs that you use? If not your cyber insurance may not cover your losses.
- Is all of your staffed trained to spot phishing emails that start this attack against your company?
- How long would it take to wipe clean your computers and reload all of your programs and data?
- Do you have a plan to operate your business while all of the pieces are put back together?
- Does your insurance cover any of these cost?
- Do you have a bitcoin wallet and do you know how to use this currency?
- How are your negotiation skills with cyber criminals?
- Do you know your local cyber crime agent at your FBI office?
Fighting back
A monitored multi layer defense for malware, viruses and ransomware will cost you $4/machine/month. Behavior monitoring blocks threats on malicious software that is not detected by other methods. Breach detection software looks for advanced hacking that can compromise your systems and network. Using a local computer account without administrator privileges stops software that can install automatically on your computer. Password managers allow for unique strong passwords for every online site and account for each user. The also allow users to share these accounts with others in your business. No longer will anyone use a Word or Excel spreadsheet to store password information. User education for current phishing emails keep everyone alert to the current tricks criminals use to compromise your systems. Encrypt your data to keep it away from unauthorized use. Use multi factor identification to verify who is using your computer assets and information. Using all of these techniques strengthens your defenses.
Your safety net
No plan is complete without insurance to provide the last level of protection. Ransomware distributors now target companies with cyber insurance, because there is less resistance to pay for a decryption key. A report by USA Today found that 61 % of data breaches target smaller businesses, causing between $84,000 and $148,000 in damages. To find the right insurance coverage consult a broker that reviews your online payment processing, how you store your intellectual property and your possible exposure to loss of client information. Cyber insurance can cover business losses, customer notification costs, forensic investigations, extortion attempts and lawsuits. Know what is covered by your policy and what requirement you have under the agreement. If you have an act of war clause in the policy you may not be covered if the attack come from a state sponsored group.
Other Threat Maps
Other vendors have live maps for attacks on systems that they protect world wide. Six other live maps include the Deteque botnet threat map , Fortinet real-time attack map , FireEye real-time cyber attack map , Bitdefender’s real-time cyber threat map , SonicWall live cyber attacks map , and the Threatbutt Internet Hacking attack map. If you have seven screens you and monitor all of these attacks at once. Do you have the resources to do this and protect from ransomware attacks? Altura IT can help you achieve your security goals. Connect with us on our contact page.