A confidential researcher determined pests in the software’s bit as well as WebKit web browser engine that are most likely part of a make use of chain.
Apple continues to put out prospective safety fires by covering zero-day vulnerabilities, launching an emergency upgrade this week to spot 3 more lately uncovered in iphone after a major software application upgrade in November already fixed 3 that were being proactively manipulated.
The freshly patched bugs become part of a safety update released Tuesday for iphone 14.4 and iPadOS 14.4. One bug, tracked as CVE-2021-1782, was located in the OS kernel, while the other two– CVE-2021-1870 and also CVE-2021-1871– were discovered in the WebKit browser engine.

The most current susceptabilities apparently weren’t recognized when Apple released iphone 14.2 as well as iPadOS 14.2, a thorough update that patched an overall of 24 vulnerabilities back in November. That upgrade included fixes for 3 zero-day imperfections discovered by the Google Project Zero group that were proactively being manipulated in the wild.
Enemies additionally may be proactively benefiting from the most recent insects, according to Apple. The firm defined the bit problem as a “a race condition” that the update addresses “with enhanced locking.” The susceptability can enable a harmful application to raise benefits if manipulated.
The WebKit susceptabilities are both reasoning issues that the upgrade addresses with improved limitations, according to Apple. Making use of these defects would permit a remote assaulter “to cause approximate code implementation,” the business claimed.
All the zero-days as well as hence the repairs impact iPhone 6s and also later, iPad Air 2 and later, iPad mini 4 as well as later, and also iPod touch (7th generation), according to Apple. Safety and security specialists think the three become part of a make use of chain aggressors can use to rise opportunities and compromise a device after its unsuspecting user succumbs to a malicious site leveraging the WebKit problem.
As is personalized, nonetheless, Apple did not explain concerning just how the bugs are being utilized in assaults, as it doesn’t usually reveal this sort of details till the majority of the impacted devices are patched.

The proliferation of apples iphone throughout the globe makes information of any type of Apple iOS zero-day a security hazard to its thousands of numerous users, and also hence a large bargain. 4 nation-state-backed sophisticated consistent risks (APTs) utilized a zero-day iPhone make use of in a very publicized espionage hack against Al Jazeera reporters, execs, anchors and also producers late last year.
Predictably, many iPhone individuals, tech specialists and protection experts required to Twitter as news of the latest spate of iOS zero-days damaged to advise iPhone individuals to upgrade their devices quickly.
” iphone release notes are always soothing when you have firsts such as this,” tweeted one iPhone user Daniel Sinclair sardonically. “3 zero-days proactively made use of in the wild. 2 entailing WebKit.”
Sinclair additionally tweeted earlier in the month that his apple iphone “inexplicably became bricked,” though it’s vague if that concern was associated with the just recently uncovered zero-days.
Assailants also might be proactively taking advantage of the most recent bugs, according to Apple. If manipulated, the vulnerability can permit a destructive application to boost advantages.
” iphone launch notes are constantly calming when you have firsts like this,” tweeted one iPhone user Daniel Sinclair sardonically. “3 zero-days actively exploited in the wild.

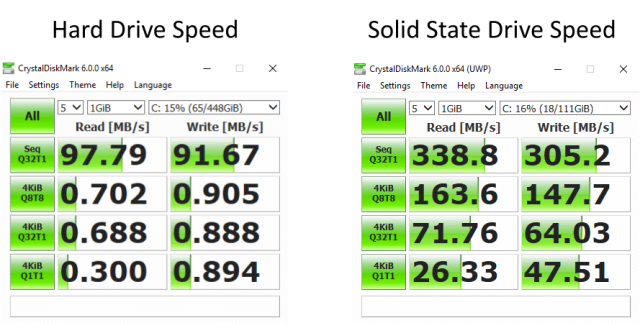
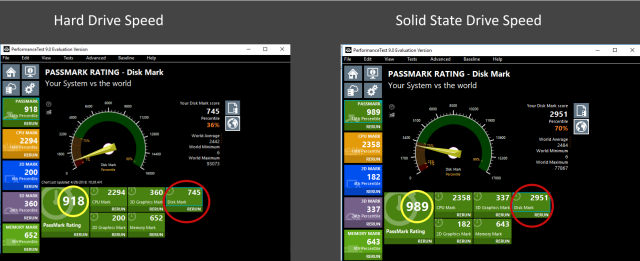

 was identified by
was identified by 

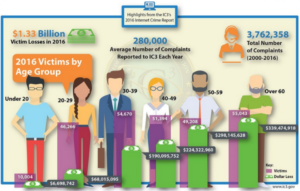
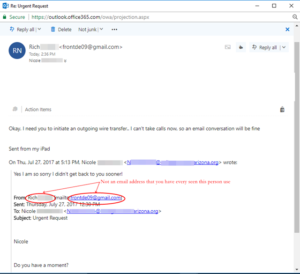 The person that received the message determined the message was a scam. That is great for her company. Are all of your employees educated on what to look for in email scams? Did you know that you can get free training videos from
The person that received the message determined the message was a scam. That is great for her company. Are all of your employees educated on what to look for in email scams? Did you know that you can get free training videos from 
 To change your Yahoo password log into your email account. Point your mouse at your name in the top right corner of the screen. Click on Account Info from the menu that appears. On the account information screen click on Account Security on the menu list on the left side of the screen. After changing your Yahoo password, find the “Disable security questions” on the left of the Account Security screen. Click on the link to clear all of you current security questions.
To change your Yahoo password log into your email account. Point your mouse at your name in the top right corner of the screen. Click on Account Info from the menu that appears. On the account information screen click on Account Security on the menu list on the left side of the screen. After changing your Yahoo password, find the “Disable security questions” on the left of the Account Security screen. Click on the link to clear all of you current security questions.